Fear As A Weapon To Get You To Open Infected Zip Files
- Published in Security
- Written by Top Speed
- Be the first to comment!
- Read: 14672 times
While not in person, this kind of email is as much an attack using social engineering as some unknown tech who shows up saying they are there to repair your copier when you weren't expecting it, but is really there to gain unauthorized onsite access to your network.
The desired outcome is the same - access! Their weapons is social engineering, cunningly forcing the person in front of them to suspend doubt and allow them access to the building (in the case of the copier repairman) or access to launch an attack on the company's network (in the case of the zip file).
The response to this email is natural, what do you mean my account was declined?!?
And before common sense kicks in the zip is opened the files extracted and wham the malicious content of the zip file is let loose on your company's network.
Rules for the new world of infected Zips:
- If you are presented with a Zip that you were not expecting do not open it until you are able to verify it's legitimacy.
- If an employee comes to you and tells you they have opened a Zip that did not contain what it was expected to contain, or appeared to contain a file that would not open or nothing at all immediately turn it off and call your tech support.
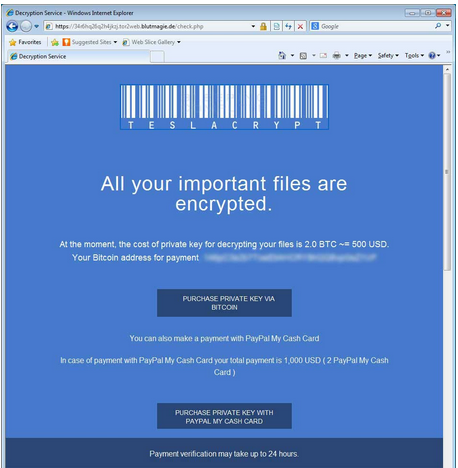
- If you find yourself face to face with one of the now numerous Ransomware screens demanding money for your data, call in an expert like Top Speed. Not all hope is lost, depending on a number of factors your company may not need to pay the criminals.
Depending on the Ransomware variant there are options that may be available in your situation. Or if you are running an Enterprise Backup Solution, where multiple versions of files are backed up, recreating a short amount of work is likely to be far more cost effective than converting USD into Bitcoins and paying the ransom.





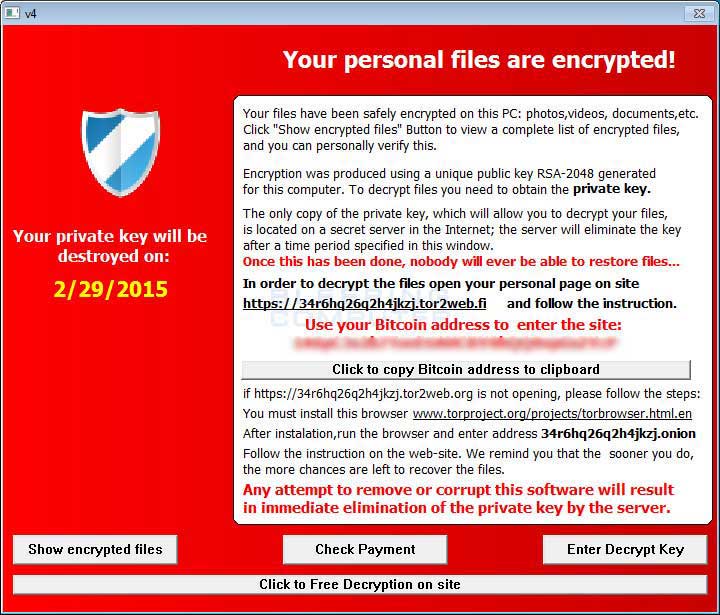 Image courtesy of Bleeping Computer
Image courtesy of Bleeping Computer