Malicious Email Disguised as Microsoft Volume Licensing Featured
This email appears perfectly legitimate although it's consequences could be devastating to a business!
Most businesses use some version of Microsoft and are aware of licensing requirements, even when they don't know the specifics of their licenses. So when an email arrives appearing to be from Microsoft's Volume Licensing Service Center and it is properly addressed to the business owner or other correct recipient within the company, most are likely to view it as legitimately from Microsoft.
Take a look at the example of this scam below. All the company and owner specifics are correct, although yes we redacted the actual business information, and as this company uses Microsoft products the owner immediately thought - I had better figure out what this is all about. 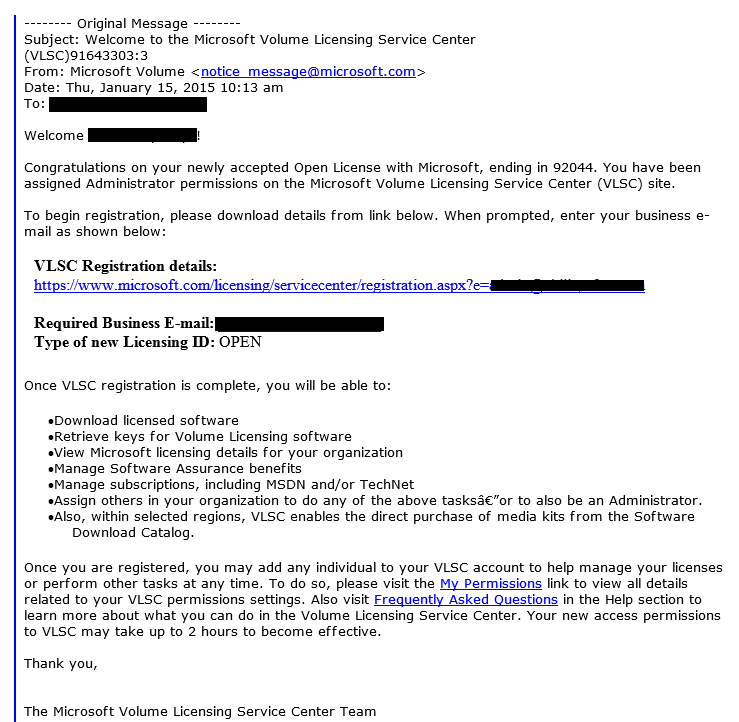
Helping to add legitimacy to this email, in the case of this business owner, is they are in the process of an expansion and are actively acquiring hardware and software, including some Microsoft products.
So what happens when the unsuspecting victim clicks on the link? That's where this rouse gets even more convincing. Upon clicking the link two things happen.
First a web browser does indeed open the main page of the Microsoft Volume Licensing Service Center. Well that definitely looks right.
Second a prompt to download and save a file also opens. The prompt is right next to the Microsoft page so this is clearly a download from Microsoft. Except it's not. The download is a zip file. As we've said over and over and over if you aren't expecting a zip file, don't save it and absolutely don't open it.
"But I thought it was from Microsoft..."
Once the zip is extracted and the program file is run it pretends to be a Screen Saver, which is an interesting choice. With monitors just going to sleep these days less and less people use screen savers so it's planting the infection in an unused portion of most people's computers.
While we didn't take the testing further, and the link in this email has been taken down preventing further testing, the download came from a Polish domain and is likely either a variant of the Dyre Malware which has previously been noted to hide as a screen saver or another method of delivery of one of the numerous versions of ransomware currently causing trouble all across the Internet.
The lesson here is the importance of vigilance. Hovering over the link before clicking shows this goes to a .pl (Polish) domain and right there no matter how good the email looks it's obviously fake. Or the moment you're prompted to do anything with a zip file that you weren't expecting either just delete it or if you believe the sender is legitimate call or email to verify the zip before extracting.

