More Records Exposed - Database Found on Google Cloud Server
- Published in Security
This case is particularly unfortunate as it represents both the intense desires entities have for our personal information and likely the more concerning problem of lax security protocols.
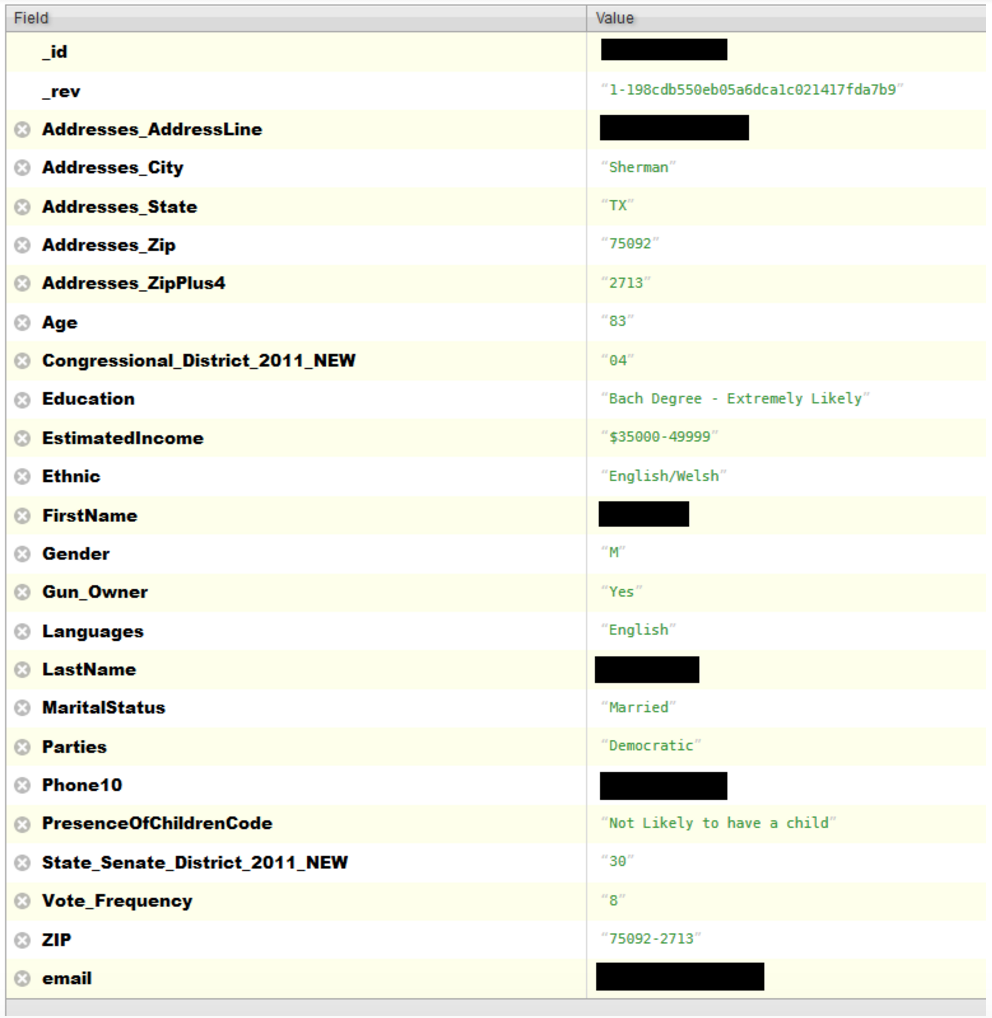
This instance revolves around a Voter database of approximately 154 million records. As anyone who does genealogy knows, voter databases are considered public records and offer a great deal of information to family researchers. However, not all voter information is included in the published records. Most states have similar laws dictating the portion of the voter registration that is public vs private; below is a general list, if you'd like to know the specifics for your state go to your state's Secretary of State website, it should have a link to voter information. Public information typically consists of your name, address, party affiliation and date of birth. The original application, social security number, and driver's license number are not to be released.
Depending on where you live additional information might also be collected: Education, Gun Ownership, Marital Status to name a few. We live in a world of data and the more data someone has on you the more targeted they can be with their advertising or more nefarious scams.
The database that has just been discovered also came with a lot of additional information not typically seen in voter databases, including Facebook profile URLs, information on children, and email addresses.
Chris Vickery / MacKeeper - Database Screenshot
The compromised database was discovered by security professional Chris Vickery. From MacKeeper it is reported that when Mr. Vickery found the database "it was configured for public access with no username, password or other authentication required." With further research Mr. Vickery was able to determine that the database was owned by data brokerage company L2. L2 was very responsive when contacted and had the database taken down and secured.
Bruce Willsie of L2 sent Mr. Vickery the following response: "Thank you for finding this and thank you for giving us the opportunity to respond. We very quickly identified the national client, informed them immediately and they took down the site as quickly as they could. The client told us that they were hacked, the firewall was taken down and then the probing began. This was an old copy (from about a year ago) of the national file and it had only a very small number of our standard fields. Needless to say, the client is doing its own research now to determine the extent of the incursion. I’ve asked that they report back to us with their findings and their plan for hardening their system in the future. It’s unfortunate and, again, we greatly appreciate your discovery of the problem."
While steps are being taken to rectify the open database, it cannot be under emphasized the damage that may have already been done by this database being open to the public.
As a part of his research Mr. Vickery also queried the server's log file. What he discovered is very concerning considering the nature of the information contained in the database. On April 11th of this year the server logged a Serbian IP address, 89.216.31.2. Serbian IP addresses are under RIPE jurisdiction and querying RIPE lists this IP address as "Fixed IP for cable modem customers". What the person did when accessing the database are either unknown or not being released. Copying the full database for sale on the black market, would be the worst case scenario, but is also most likely what occurred.
As individual's value lies in the data collected on them, there is a good chance someone no one wants having information on them, now knows a great deal more than they should!